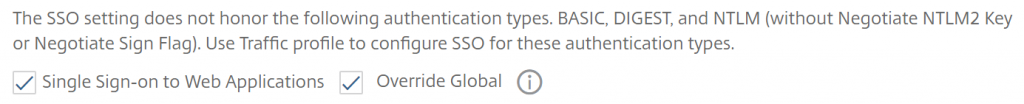
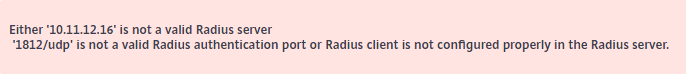
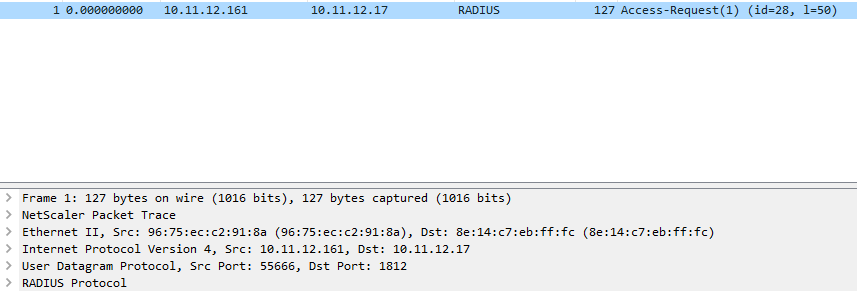
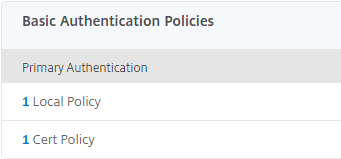
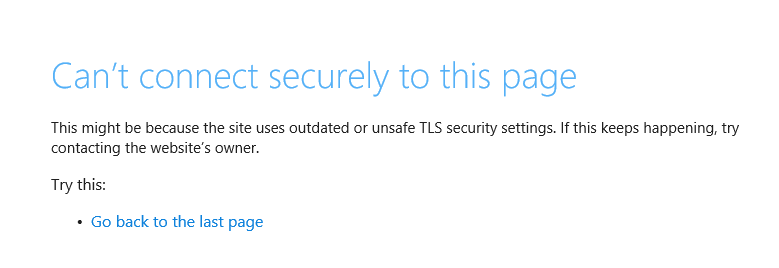
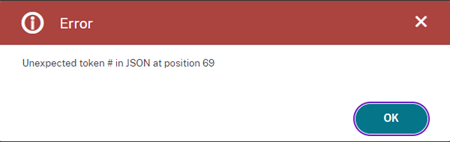
After Citrix implemented the security of ns.conf with the KEK keys I have notices that the “Test Network connectivity” through an error in the GUI:
Well, how do we the test the LDAP configuration and connection?
This can be done by the CLI, in shell mode 😊
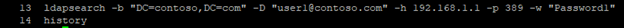
From the shell mode you can run the following command to test the LDAP configuration:
ldapsearch -b “DC=contoso,DC=com” -D “user1@contoso.com” -h 192.168.1.1 -p 389 -w “Password1”
If your username and password are not valid you will get something like this:
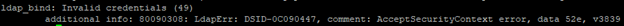
If there are connection to a Domain Controller and username and password are valid you will receive information of the users in the Active Directory.
So, we can use the CLI shell mode to test the LDAP connection and validate the username and password. But there is one problem. To test we need to type the password in clear text. In my blog “NetScaler CLI, Watch Out” I wrote about the “history” of the CLI commands and that password in clear text are stored until the Citrix ADC is rebooted.
We have the same problem when we test the LDAP connection when using CLI in shell mode. If I run the “history” command I get this:
It is therefore my recommendation that you create a temporary user account on the Citrix ADC. Then run the command to test the LDAP. And finally remove the temporary user account.
By doing this the password for the LDAP users can not be accessed through the “history” command.