Some customers currently experience high outgoing traffic from there Citrix ADC/NetScalers. Citrix has reported more about this in there article here:
The fix is to upgrade to one of these versions:
- Citrix ADC and Citrix Gateway 13.0-71.44 and later releases
- NetScaler ADC and NetScaler Gateway 12.1-60.19 and later releases
- Citrix ADC 12.1-FIPS 12.1-55.210 and later releases
- NetScaler ADC and NetScaler Gateway 11.1-65.16 and later releases
Or you can disable DTLS.
In their article it is describe how-to disable DTLS on the Citrix Access Gateway configuration, but if you have a Content Switch in front this will not do it as the client session it terminated on the Content Switch vServer.
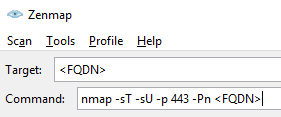
A quick test to show that:
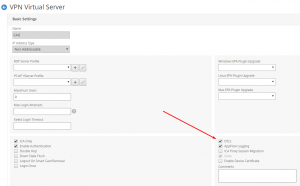
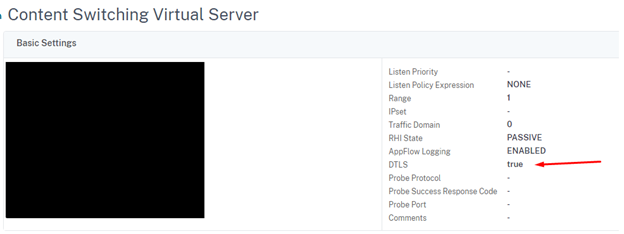
My Content Switch vServer configuration:
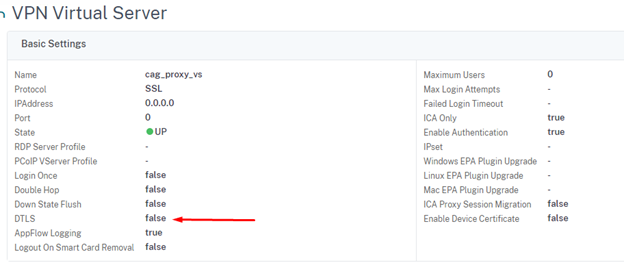
My Access Gateway vServer configuration:
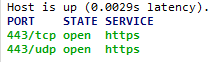
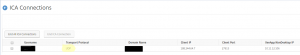
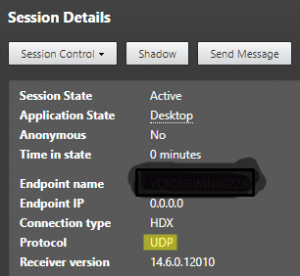
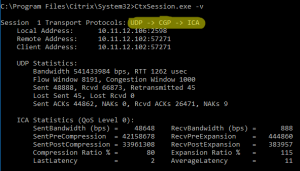
When I make a Citrix Session, I get this:
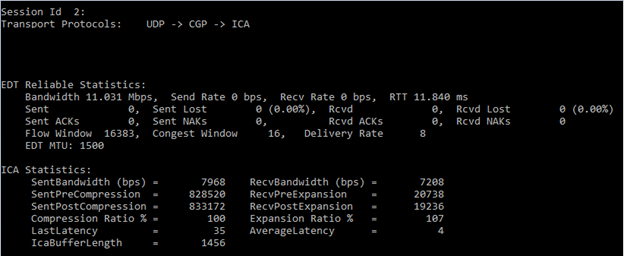
As you can see this Citrix Session is using DTLS.
If you have a Content Switch in front of your Access Gateway function you need to disable DTLS on the Content Switch configuration, or else you are still vulnerability for the DDoS attack. This is missing from the Citrix article.