This blog is from a lesson learned in the field. I have done a normal upgrade from 11.1 to 12.1 on a Citrix ADC HA pair. After the upgrade users complained that they get an error when logging in to some Web sites that where protected by a Security Server on the ADC.
We found that the sites where all located in a Partition on the ADC.
LDAP test run without any error.
Radius test give this error:
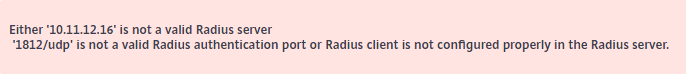
Ok, the problem where with the MFA Radius authentication.
To debug I run a nstrace from the partition:
- switch partition radius_test
- start
nstrace -size 0 -filter CONNECTION.PORT.EQ(1812)
- Did the Radius test and got the error again
- stop nstrace
But there where no trace files in /var/partition/radius_test/nstrace. I did this again but still no trace files.
What was going on???????
After some more debugging I did a trace on Default partition, and now I got some data in my trace:
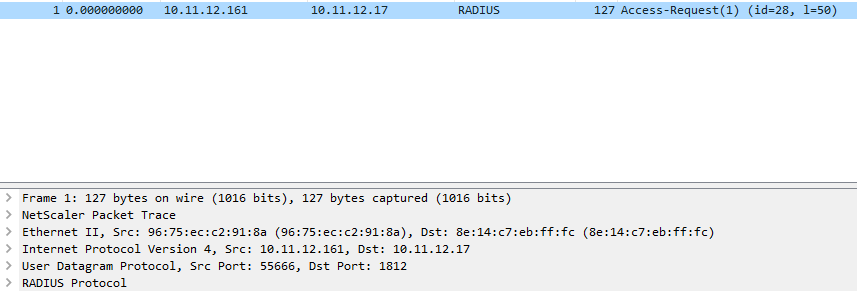
But the request was coming from the NSIP and not from the SNIP in the partition. Do to Firewall configuration the Radius server could not be accessed this way.
It turns out that the Radius test is done from the default partition. You can’t use the test with in at partition as the request is not send from the source address you think.
I later found this in ns.log:
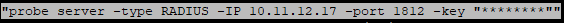
The learned lesson is that if you use Partitions, you can not relay on the Radius test function, as this may not give you a correct response, do to the way traffic is going out of the ADC.
We found a bug in ADC 12.1 build 55.18. Challenge-Response Radius request from a Partition got stuck at the ADC, and the users never received their token, and where not prompted for it.
As the ADC 11.1 build 63.15 had the same bug from default partition, we ended up with a total rollback, and is now waiting for Citrix to fix this.