With the new release of Citrix XenDesktop/XenApp 7.16 the HDX Adaptive Transport it now turned on by default.
With that turned on, clients connecting through NetScaler Gateway will try to connect using UDP 443. If Firewall and NetScaler Gateway is not configured to communicate on UDP 443, the client will fallback to TCP 433.
I have noticed that it takes a short time before it will do the fallback (2-5 sec.). This give a longer logon time when the users are connecting through NetScaler Gateway. With the right configuration, you can eliminate that extra wait time for the users.
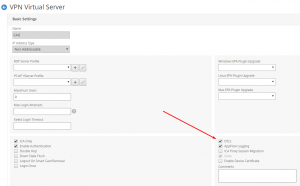
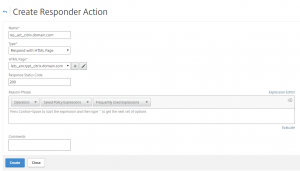
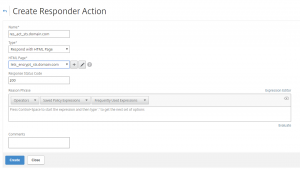
First, enable DTLS (Datagram Transport Layer Security) on the NetScaler Gateway configuration:
After enabling DTLS, you need to rebind the Server Certificate again. Do a unbind and a bind, then it will work.
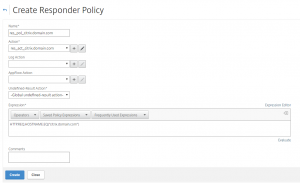
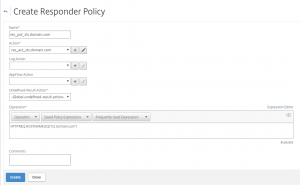
The next is to enable UDP 443 on the Firewall Access and NAT rules. As there are many different Firewall’s I cannot tell you the way to do it one your Firewall.
I found that you can use nMap/Xenmap to test if your configuration of the Firewall and NetScaler Gateway configuration.
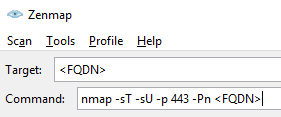
Use the flowing command to do the test:
nmap -sT -sU -p 443 -Pn <FQDN>
The test has to be run from a external computer, as we are testing the Firewall and NetScaler Gateway configuration.
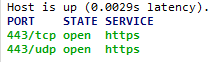
This will test TCP 443 and UDP 443, and give this result if you’re Firewall and NetScaler Gateway is configured to accept TCP 433 and UDP 443:
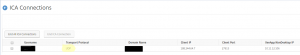
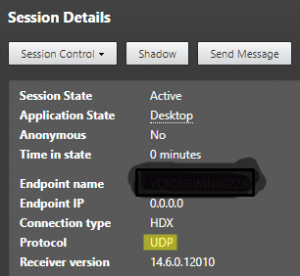
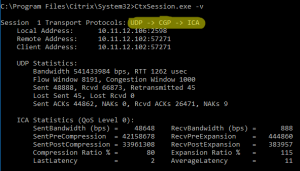
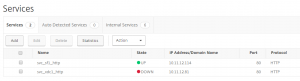
There are different ways to see if a user is connected using UDP 443.
NetScaler Gateway GUI:
NetScaler Gateway CLI:
XenDesktop/XenApp Director:
Server/VDI VDA:
Citrix HDX Adaptive Transport, Datagram Transport Layer Security is supported with Citrix Receiver 4.7 or newer.