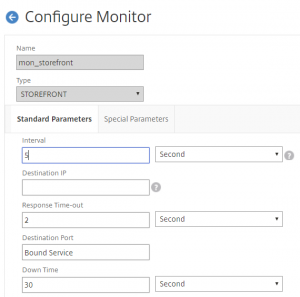
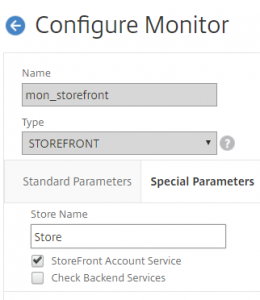
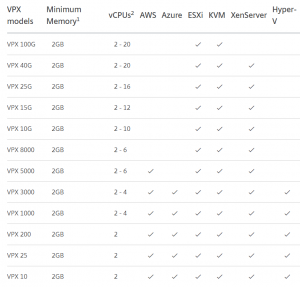
You can use the NetScaler to make GEO IP filter to your Web Sites. This can enhanced your security, as traffic only from specified countries is allowed. You can have Web Sites with data you don’t wont specified countries to access.
You can also use it to send users from specified locations to specified Web Sites, with are customized for them.
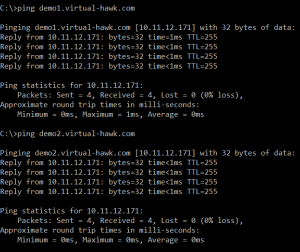
In the flowing example I simply block all traffic not from DK locations.
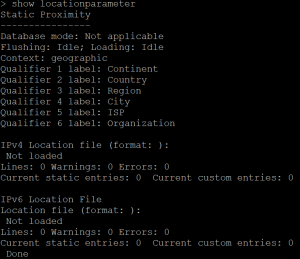
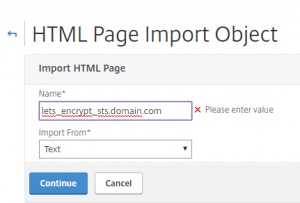
First check if your GEO IP is imported:
Update:
In the new build of Citrix ADC/NetScaler the GEO IP Database is included. You only need to enable the Citrix ADC/NetScaler to you it:
add locationFile /var/netscaler/inbuilt_db/Citrix_Netscaler_InBuilt_GeoIP_DB_IPv4
set locationParameter -matchWildcardtoany YES
***** Old blog, start *****
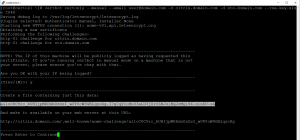
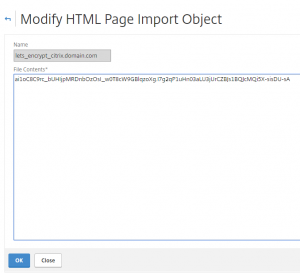
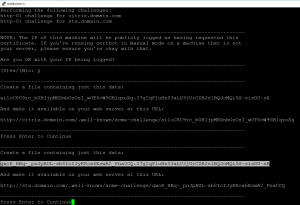
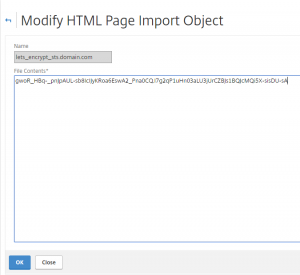
If status is “Not Loaded” upload the GEO IP Database to /var/geoip
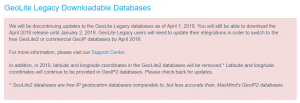
I have downloaded the GEO IP Database from http://geolite.maxmind.com/download/geoip/database/GeoIPCountryCSV.zip
Unforcedly this is a legacy database and maintains of this will stop, but for testing the configuration it will be fine. This is the statement from MAXMIND:
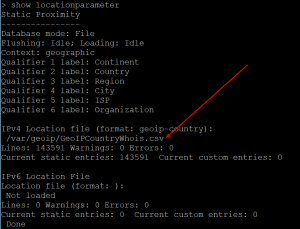
After uploading the file “GeoIPCountryWhois.csv” to the /var/geoip/ you need to configure the NetScaler to load it:
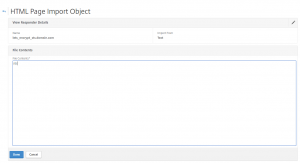
Control that it is loaded:
As after NetScaler Version 11.1 Build 53.11 you need to enable wildcard search, with this:
***** Old Blog, end *****
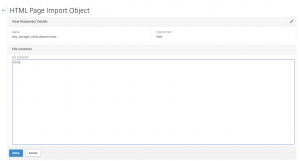
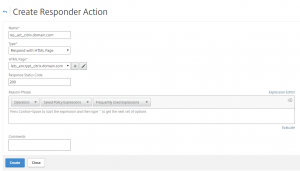
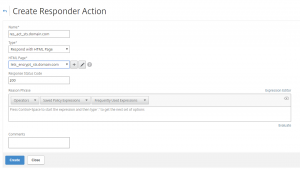
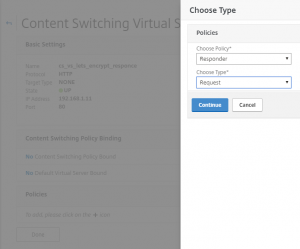
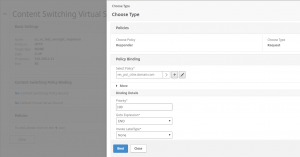
For testing, I have made a response action:
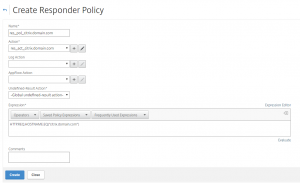
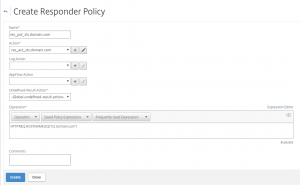
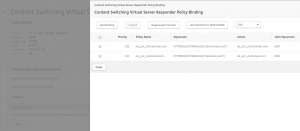
And a response policy:
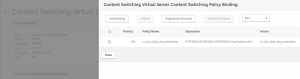
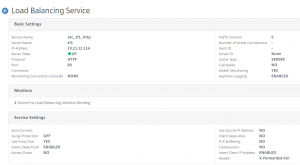
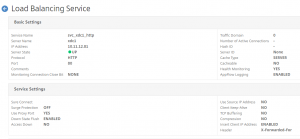
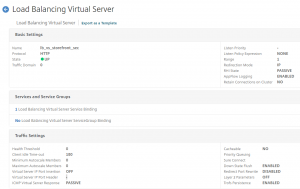
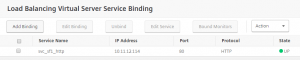
Now bind the responder policy to the Load Balancing vServer, and test.
To trigger a block a simply change the DK to another country, as I have no way to test from other than DK IP addresses. When changing to SE, I get the flowing message when testing:
I recommend that you simply use a drop, to hide that you actually make the GEO IP check. You can do that with:
Conclution:
GEO IP can be used to enhanced your security as you can set a policy to witch country that are allowed to access a Web Site or a Access Gateway.
You can use GEO IP to send users to specified Web Server based on their public IP Adresses.
CLI Commands:
show locationparameter
add locationfile /var/geoip/GeoIPCountryWhois.csv -format GeoIP-Country
set locationParameter -matchWildcardtoany YES
add responder action res_act_display_blocked_page respondwith “\”Sorry, the IP address you are connecting from (\”+CLIENT.IP.SRC+\”) is detected as untrusted. Access to our systems from your location is not allowed.\””
add responder policy res_pol_drop_non_dk “CLIENT.IP.SRC.MATCHES_LOCATION(\”*.DK.*.*.*.*\”).NOT” res_act_display_blocked_page
set responder policy res_pol_drop_non_dk -action DROP