Once again, a was struggling to get User Certificate Authentication to work, until I suddenly remembered why:
You cannot put your Certification Authentication Virtual Server behind a Content Switching Virtual Server.
You can, but then you must enable Client Authentication on the Content Switching Virtual Server, and as this often have a lot of other web sites configured all of them will have Client Authentication enabled.
The reason for this is that when you use Content Switching Virtual Server the SSL session is established to this and the you need Client Authentication configured here.
So, if you have a special web site that you need to protect with Client Authentication you need a direct accessible Authentication Virtual Server.
Let me show the configuration I ended up with:
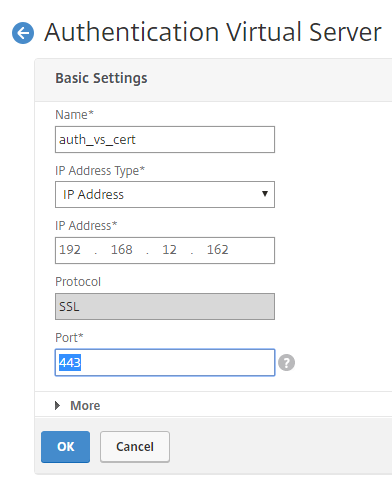
Create an Authentication Virtual Server:
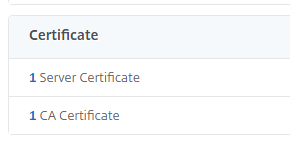
Bind your public certificate and your root ca certificate:
For test a use a local user account, but this is normal an Active Directory account:
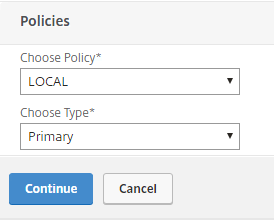
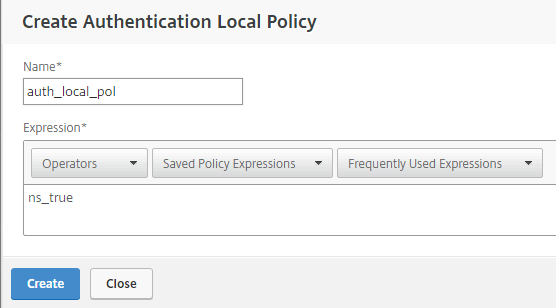
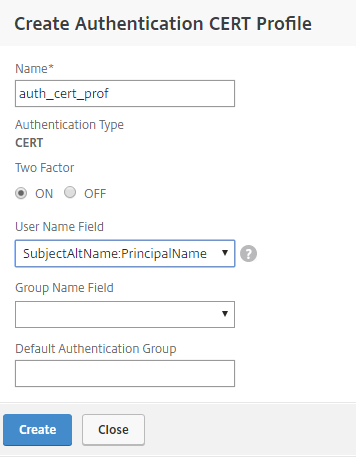
Then add the Certificate Authentication policy:
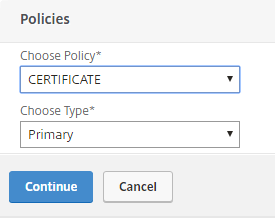
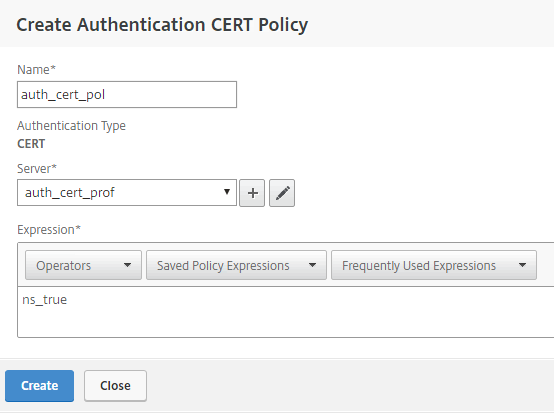
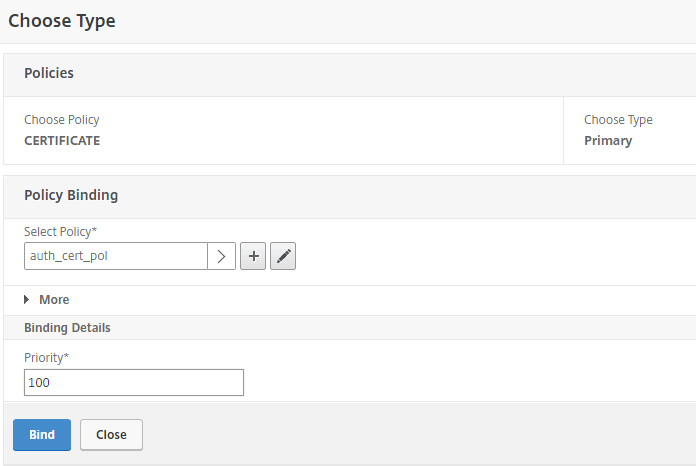
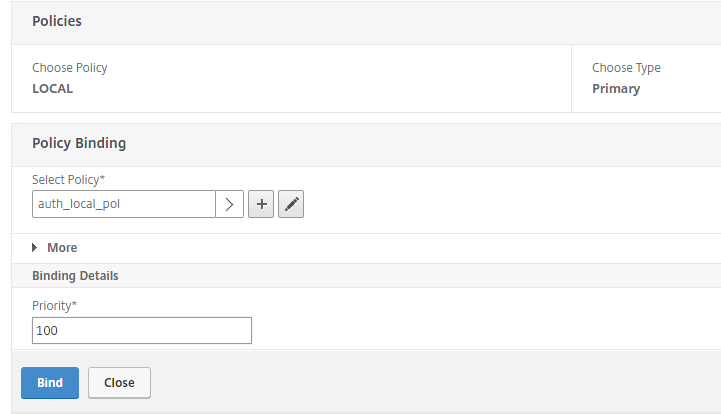
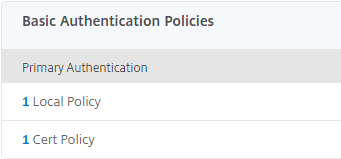
You will end up with 2 primary authentication policies:
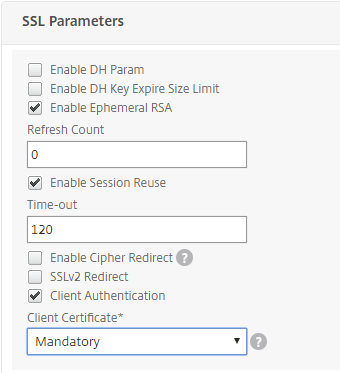
Change the SSL Parameters so that Client Authentication is enabled:
Now create the Load Balancing Virtual Server and enable Authentication on this:
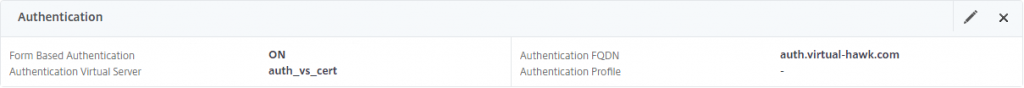
That is, it, and when we test, we will get this.
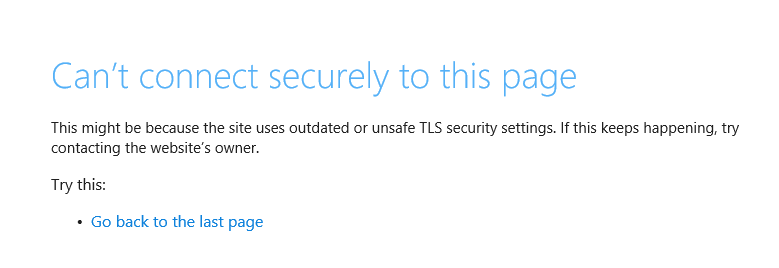
When testing with a user that have no certificate the site will close the connection:
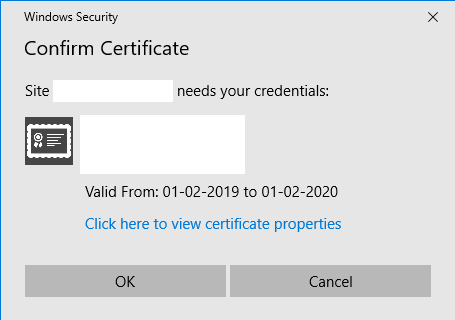
And testing with a user that have a certificate the user is prompted for the certificate to use:
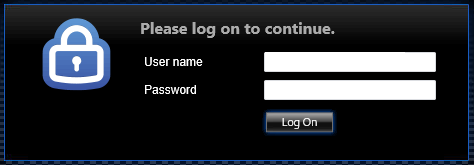
After selected the certificate, the user is redirected to the Authentication Virtual Server for logon:
Conclusion:
You can use User certificates when protecting web sites with authentication. Just remember that the authentication virtual server can often not be behind a content switching server as this will enable user certification on all web site configured on the content switching server.